Social engineering is a non-technical method of breaking into a system or network. Social engineering is important to understand because hackers can use it to attack the human element of a system and circumvent technical security measures. This method can be used to gather information before or during an attack.
A social engineer commonly uses the telephone or Internet to trick people into revealing sensitive information or to get them to do something that is against the security policies of the organization. By this method, social engineers exploit the natural tendency of a person to trust their word, rather than exploiting computer security holes. It’s generally agreed that users are the weak link in security; this principle is what makes social engineering possible.
Human-Based Social Engineering:
Human-based social engineering refers to person-to-person interaction to retrieve the desired information. An example is calling the help desk and trying to find out a password.
Computer-Based Social Engineering:
Computer-based social engineering refers to having computer software that attempts to retrieve the desired information. An example is sending a user an email and asking them to reenter a password in a web page to confirm it. This social-engineering attack is also known as phishing
Human-Based Social Engineering Methods:
- Impersonating an Employee or Valid User
A hacker can gain physical access by pretending to be a janitor, employee, or contractor. Once inside the facility, the hacker gathers information from trashcans, desktops, or computer systems. - Posing as an Important User
In this type of attack, the hacker pretends to be an important user such as a high-level manager who needs immediate assistance to gain access to a computer system or files. - Using a Third Person
a hacker pretends to have permission from an authorized source to use a system. This attack is especially effective if the supposed authorized source is on vacation or can’t be contacted for verification. - Calling Technical Support
Calling tech support for assistance is a classic social-engineering technique. Help desk and technical support personnel are trained to help users. - Shoulder Surfing
Shoulder surfing is a technique of gathering passwords by watching over a person’s shoulder while they log in to the system - Dumpster Diving
Dumpster diving involves looking in the trash for information written on pieces of paper or computer printouts.
Computer-Based Social Engineering Methods:
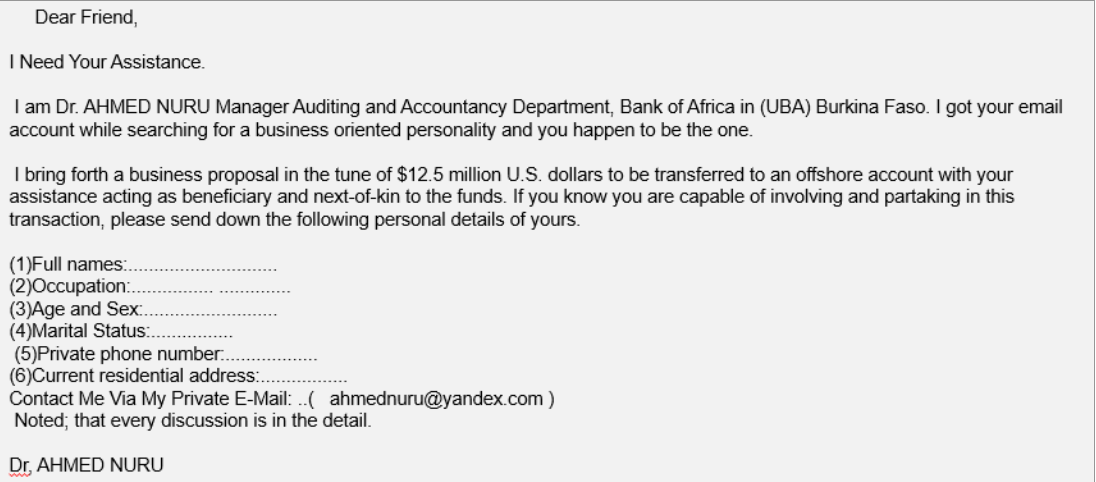
- Email attachments
example:
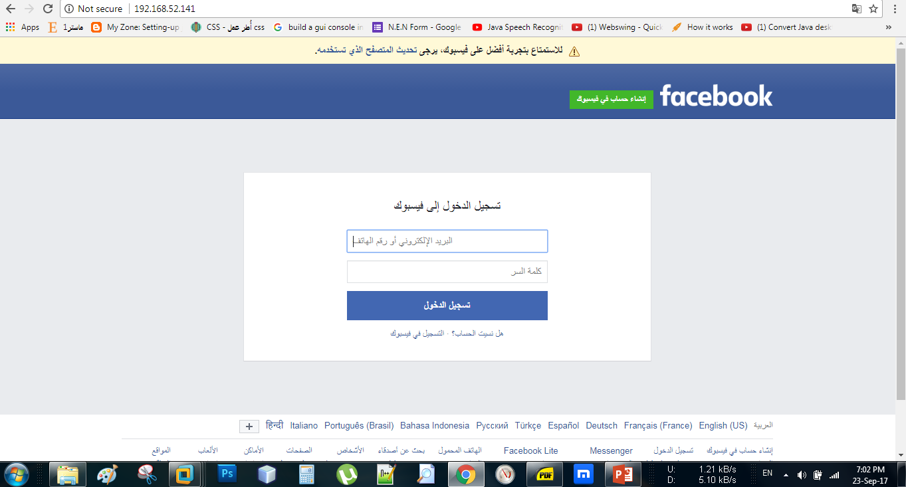
- Fake Websites (Clones):
This is a fake Facebook login page used to harvest users credentials
How to protect your self
- Think before you click. Attackers employ a sense of urgency to make you act first and think later in phishing attacks. When you get a highly urgent, high-pressure message, be sure to take a moment to check if the source is credible first. The best way is to utilize another method of communication different from where the message is from – like texting the person to see if they emailed you an urgent message or that was from an attacker. Better be safe than sorry!
- Research the sources. Always be careful of any unsolicited messages. Check the domain links to see if they are real, and the person sending you the email if they are actual members of the organization. Usually, a typo/spelling error is a dead giveaway. Utilize a search engine, go to the company’s website, check their phone directory. These are all simple, easy way to avoid getting spoofed. Hovering your cursor on a link before you actually click on it will reveal the link at the bottom, and is another way to make sure you are being redirected to the correct company’s website.
- Email spoofing is ubiquitous. Hackers, spammers, and social engineers are out to get your information, and they are taking over control of people’s accounts. Once they gain access, they will prey on your contacts. Even when the sender appears to be someone you are familiar with, it is still best practice to check with them if you aren’t expecting any email links or files from them.
- Don’t download files you don’t know. If you (a) don’t know the sender, (b) don’t expect anything from the sender and (c) don’t know if you should view the file they just send you with “URGENT” on the email headline, it’s safe not to open the message at all. You eliminate your risk to be an insider threat by doing so.
- Offers and prizes are fake. I can’t believe I’m still saying this in the big year of 2018, but if you receive an email from a Nigerian prince promising a large sum of money, chances are it’s a scam


